Barcotec mCloud
Make an inquiry

Unified Endpoint Management – powered by Barcotec & 42Gears
With the user-friendly mCloud Endpoint Management, you can easily manage and secure all your devices centrally - from mobile computers to tablets and printers.
Simple operation: Based on the globally used UEM from 42Gears
Secure technology: Hosted by Barcotec in Austria and continuously developed further
Powerful features at transparent and stable prices
Local support: expert team with extensive knowledge
Live demo
Arrange a short demonstration via video call now. In around 30 minutes, our team will show you how easy it is to add devices to the mCloud and the most important functions and features for your needs.
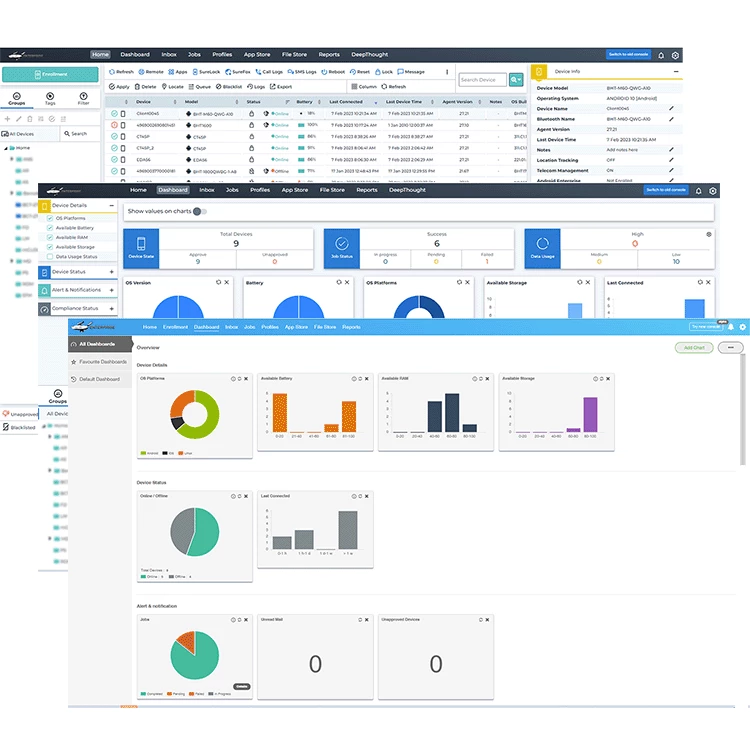
The most important functions
Central configuration and management of devices, apps, settings and content
Kiosk mode for simple and secure device operation - you decide which applications and functions are available on the devices
Automatic e-mail alerts for efficient monitoring and reporting
Integrated remote access to the devices for direct support and fast problem solving
Remote deletion of data in the event of unauthorized users, loss or theft of the device
Compatible with: Android, iOS/iPadOS, macOS, Windows, Linux, Chrome OS, wearOS and smart glasses
Optimized for modern devices
In addition to the simple management of smartphones, tablets and PCs, mCloud Endpoint Management offers in-depth access to OEM-specific functions. Whether special scanner settings or efficient battery management, with mCloud you can get the most out of your mobile computers, tablets and vehicle terminals!

Personal support
The Barcotec mCloud team advises and supports you from the initial configuration through to the automation of tasks for ongoing operation. If you have any questions or problems, you have immediate access to highly qualified experts, and 3rd-level support for ongoing operations is included in our clearly structured pricing.
About 42Gears
Founded in 2009 by two mobile data capture device specialists, 42Gears' UEM now secures over 5 million devices in 115 countries. 42Gears works closely with Google and is an Android Enterprise Gold Partner.
The company is characterized by a particularly strong customer focus. This is a very valuable feature in the cooperation with Barcotec, new requirements of our customers are implemented together with 42Gears in the shortest possible time and thus enable a continuous expansion with useful functionalities.

Reduce costs with endpoint management
Our interactive ROI calculator shows you quickly and transparently what cost savings you can achieve with a modern UEM.